Hate speech sanitizer
Posted by Austin Morris on UTC 2019-10-26 16:14
First-time users should consult the notes below.
Step 1: Type or paste a text (>60 and <1024 chars) for the encryption key, or just press Generate .
Step 2: Type or paste your text into the input box. Press Encrypt .
Step 3: EITHER press Select to copy the encrypted text onto the clipboard, OR press Obscure to render the encryption in plain text.
Step 4: Press Select to copy the encrypted text onto the clipboard.
Step 5: The recipient of your text just has to paste it into the appropriate box on this page – steganography or encryption – and press the relevant button, Expose or Decrypt .
Notes
- There was a young man from…
- STOP!
STOP THAT RIGHT NOW!
Take your hands off the keyboard and step away from that limerick. NOW!
If you have ever wanted to share some possibly quite offensive text with people you know who can appreciate the finer points of offensiveness – and yet wanted to avoid causing offence to the easily offended, here is the tool for you.
Background and credits
This tool has been derived from John Walker's JavaScrypt project on his fascinating website Fourmilab, where he was kind enough to put his code in the public domain for everyone to steal. Those who need more information should consult John Walker's extensive and exemplary documentation on his website. We have made some code and cosmetic tweaks in order to adapt his implementation to our website.
John's creation of JavaScrypt, that is, a JavaScript encryption library, has two great advantages over heavyweight encryption solutions: it is easy to use and nothing leaves your browser. There is no tracking or communication with the outside world; your text, whether clear or encoded, is not sent anywhere else. There are no backdoors or workarounds: without the relevant key there can be no decryption.
[Note for the paranoid: text in webforms can often be very 'sticky' – that is, it often stays in the text field even when the page is reloaded. This does not mean that the text has been saved or sent somewhere. It will disappear in due course, but if you are in a hurry a click on Clear will dispose of it permanently.]
1— Encryption keys
Like every other encryption utility this tool uses a key to encrypt a text. You will need to give this key in some discrete way to the people with whom you wish to share the contents of your degenerate mind. If someone in turn passes it straight on to the Powers-That-Be, you will at least find out who your true friends aren't. Win-win.
- For good quality encryption the key should be at least 60 characters (~12 words) long. It should not be longer than 1024 characters: the field will not allow you to enter more than that anyway.
- You can make up your own key by typing in a text. The use of the unusual characters so loved by old-fashioned login systems is completely unnecessary here. Just beware of whitespace characters either before or after your key – you may not be able to see them but they will be treated as part of the key.
- The easiest way to get a shareable key is to paste in a string from an existing piece of text – for example: 'The breezy call of incense-breathing Morn, The swallow twitt'ring from the straw-built shed,' (92 characters). Your recipient has to reproduce this string exactly, of course, which means you both have to make sure that you use the same source for your key text and be accurate about spelling, spacing and punctuation.
- Alternatively, pressing Generate will create a key for you. You can choose to generate the key as a string of ANSI characters or a string of hexadecimal characters. How you distribute this odd-looking phrase to your recipient(s) without arousing suspicion is your problem.
- Press Select to copy the key onto the clipboard.
2— Encrypting text
Type or paste the text you want to encrypt into the input box. The text can be as long as you like (within reason). Images cannot be encrypted of course, but links are treated as conventional text. When you have done that, press the Encrypt button. The encrypted text will appear in the pink text area.
Once again, the customer is king or queen: you can choose whether you want the encrypted text output in code groups or in strings of hexadecimal or base 64 characters. It doesn't matter which you choose – they will all work.
Press Select to select the entire text and copy it onto the clipboard. You can now paste this encrypted text into website fields, comment threads and social media messages – anywhere that will accept text.
3— Switch off the Christmas lights
Anyone looking at this sequence of characters will realise that this is encrypted text and that consequently you have something to hide. The Powers-That-Be have monitoring services that will be triggered by encrypted text. On most social media providers your encrypted text will attract the attention of the systems that monitor such things as a lit up Christmas tree attracts the child's gaze.
The solution to this problem is to use some form of steganography to make your message less conspicuous – although the text will still look odd to the careful reader. This tool offers a steganography option which will output your encrypted text as a string of plain English words. If the steganographic text makes more sense than your normal unencrypted writings you should consider taking advice. Note that the steganographic process does not encrypt your text, it just makes it less obviously encrypted.
With the encrypted text still in its field, press Obscure . Press Select to select the entire text and copy it onto the clipboard.
Leave the checkbox 'Sentinel' checked. Consult the Fourmilab documentation if you want to know what this setting does.
4— Decrypting text
If you receive a steganographic text, you just need to paste it into the steganography field and press Expose to copy the encrypted version of the message into the encryption field. Note that a steganographic text can be converted back to an encrypted text without a key.
A key is of course required to decrypt the encrypted text and should be entered into the key field now. Pressing Decrypt will write the decrypted text into the plain text field. You can now read about the jolly goings on that were to be seen from the bridge at Buckingham without worrying that anyone has been upset by this cheerful limerick.
Of course, if your correspondent sent just unobscured encrypted text, paste this into the encryption field and then press Decrypt .
Health warnings
Why, the reader asks, are we aiding and abetting potential criminals, cheats, philanderers, pimps, tinfoil-hatters and other assorted riff-raff?
Well, that's a good question, which we shall consider fully on another occasion. There are those still alive (just) who can remember a time when western society was founded on ideas of confidentiality and privacy – not every act, thought or utterance took place within the view of the observational platform of a state Panopticon, as it does today.
The system presented here is clearly unsuitable for use in engineering the overthrow of a government. However, on current form, most governments in the western world are doing a cracking job of overthrowing themselves.
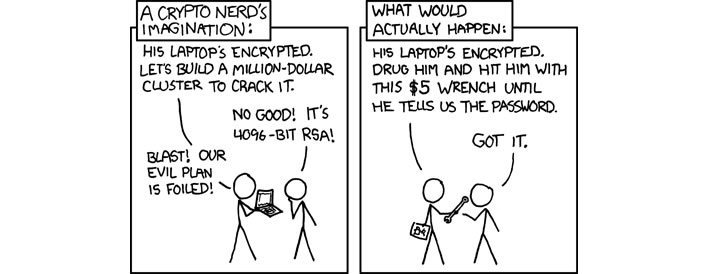
A word of warning, however: you may know that your encrypted texts contain only the sort of harmless vulgarity that has been enjoyed by consenting adults in private down the centuries, but please note that the Powers-That-Be do not know this and may be moved to pay you a visit. In which case the second option will apply:
0 Comments UTC Loaded:
Input rules for comments: No HTML, no images. Comments can be nested to a depth of eight. Surround a long quotation with curly braces: {blockquote}. Well-formed URLs will be rendered as links automatically. Do not click on links unless you are confident that they are safe. You have been warned!